The Death of Ransomware?
 Malicious software – dubbed malware – is any software that goes against the interest of the computer user. Ransomware is a type of malware and it’s particularly nasty. It takes your data hostage, encrypting it and thus making it inaccessible. The only way to access your data again is by entering the magic password. Unfortunately for victims, the password is not simply “Open Sesame”. The only way to get that password is to pay a ransom to the cybercriminal – generally in untraceable cryptocurrencies such as Bitcoin. In actual fact, 70% of the time the criminal in question does give you your data back – otherwise the bad reputation of never restoring the data would mean no one would ever pay up! But, ransomware’s time at the top has reportedly ended – a new kingpin is in town.
Malicious software – dubbed malware – is any software that goes against the interest of the computer user. Ransomware is a type of malware and it’s particularly nasty. It takes your data hostage, encrypting it and thus making it inaccessible. The only way to access your data again is by entering the magic password. Unfortunately for victims, the password is not simply “Open Sesame”. The only way to get that password is to pay a ransom to the cybercriminal – generally in untraceable cryptocurrencies such as Bitcoin. In actual fact, 70% of the time the criminal in question does give you your data back – otherwise the bad reputation of never restoring the data would mean no one would ever pay up! But, ransomware’s time at the top has reportedly ended – a new kingpin is in town.
Cryptojacking
Never heard of it? Neither had I until only very recently. This is probably because of how it operates – inconspicuously. So what is cryptojacking? Well it’s essentially unauthorised cryptomining.  Cryptomining is like your computer entering the lottery and it picking random numbers. The jackpot is having a number match the answer to complex m athematical problem (known as ‘proof of work’). The first computer to get the right number gets the jackpot of being rewarded with cryptocurrency – i.e. Bitcoin pays for the ‘proof of works’ to be solved. Mining like this is completely legal, however it is massively resource intensive. So much so that one person mining solo is typically unfeasible. The more lottery numbers your computer can generate per second, the greater the chance of you being successful. Most commonly, groups of people work together and make a pool, then share the winnings. Cybercriminals are exploiting this and hijacking other people’s computers in order to mine more efficiently. By doing this, they build up a mining network or pool which speeds up the mining process. Simply put, the more processing power they have, the more money they make. They either install mining software on unsuspecting user’s computers, or (much more commonly) insert a mining code into websites, unbeknownst to the site owners. This code then runs a mining programme, using up to 80% of the user’s processing power.
Cryptomining is like your computer entering the lottery and it picking random numbers. The jackpot is having a number match the answer to complex m athematical problem (known as ‘proof of work’). The first computer to get the right number gets the jackpot of being rewarded with cryptocurrency – i.e. Bitcoin pays for the ‘proof of works’ to be solved. Mining like this is completely legal, however it is massively resource intensive. So much so that one person mining solo is typically unfeasible. The more lottery numbers your computer can generate per second, the greater the chance of you being successful. Most commonly, groups of people work together and make a pool, then share the winnings. Cybercriminals are exploiting this and hijacking other people’s computers in order to mine more efficiently. By doing this, they build up a mining network or pool which speeds up the mining process. Simply put, the more processing power they have, the more money they make. They either install mining software on unsuspecting user’s computers, or (much more commonly) insert a mining code into websites, unbeknownst to the site owners. This code then runs a mining programme, using up to 80% of the user’s processing power. 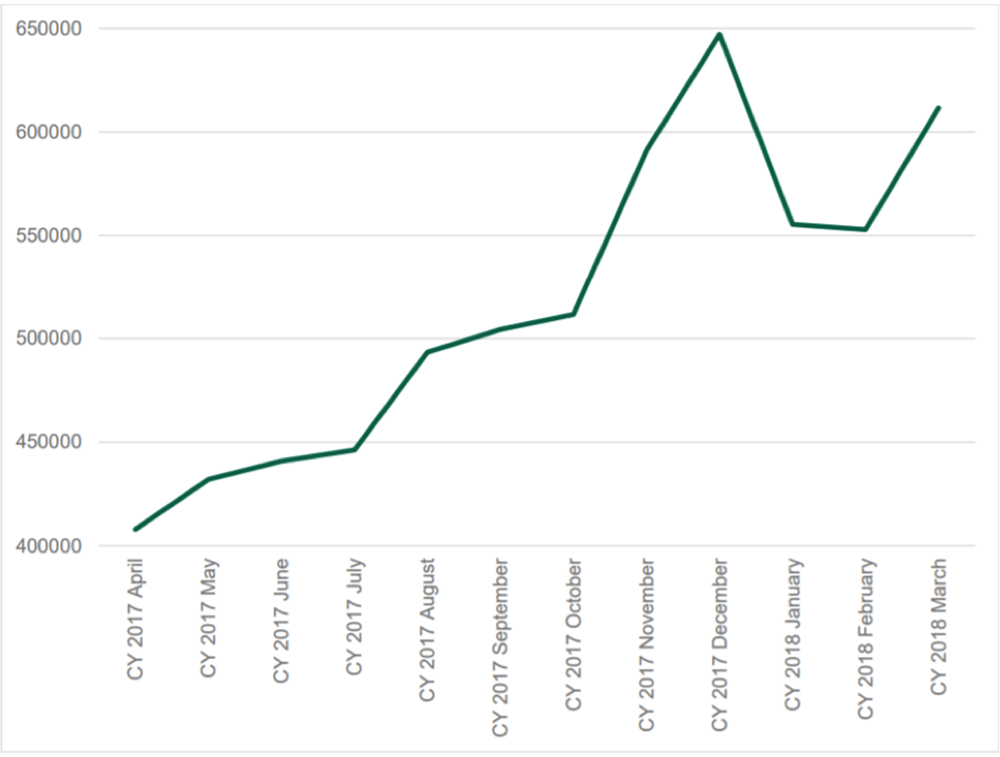 The two most common currencies used for mining are Monero (XMR) and Zcash as they guarantee anonymous transactions. There is a definite trend in mining activity as it coincides with the currency’s value – the dip in the graph at January 2018 below coincides with a dip in the value of both Bitcoin and Monero. Up to $30k a month can be generated from a mining network but even this is a conservative estimate! Even though ransomware is on the decline, don’t get too comfortable. I can’t see it disappearing completely as the temptation of a ‘quick buck’ is too great for cybercriminals.
The two most common currencies used for mining are Monero (XMR) and Zcash as they guarantee anonymous transactions. There is a definite trend in mining activity as it coincides with the currency’s value – the dip in the graph at January 2018 below coincides with a dip in the value of both Bitcoin and Monero. Up to $30k a month can be generated from a mining network but even this is a conservative estimate! Even though ransomware is on the decline, don’t get too comfortable. I can’t see it disappearing completely as the temptation of a ‘quick buck’ is too great for cybercriminals.
Why ransomware refuses to go away
There are two types of ransomware – blockers and encryption. The difference being the damage blockers do can be fully reversed, sometimes even from just reinstalling the operating system. Encryption on the other hand can’t be solved so easily, in fact, the best ransomware encryption is mathematically impossible to crack! Back in 2013, CryptoLocker started a new-age of ransomware and at its peak, over half a million machines were infected. Combining all its variants (such as CryptoWall, which accounted for half of all ransomware attacks in 2014-15) CryptoLocker harvested nearly $3,000,000 of ransom fees. On average, the cybercriminals charged $700 for the key to unlock an infected individual’s data.
Preventing instead of reacting is key. If you are reacting to a breach in security or after malware is already on your computer, then really it’s too late
Developed countries are targeted for ransomware whereas cryptojacking is generally targeted at developing countries. A likely reason for this is that the developing countries are less likely to be able to pay the ransom demanded. Cybercriminals won’t cease to use ransomware just because cryptojacking is now on the scene. The quick buck is far too tempting albeit less dependable. With cryptojacking, the cash flow is steady and constant but takes longer to raise the same capital as ransomware.
How to defend against them
Preventing instead of reacting is key. If you are reacting to a breach in security or after malware is already on your computer, then really it’s too late. The cybercriminals could have access to all your data already! In early 2017, the trend for who was targeted by ransomware changed. Instead of mainly home-users, cybercriminals attention turned to businesses. So making sure your businesses security is attack-proof is more critical than ever. Make sure your company is protected – click here