PARTNER NEWSFEED
Industry
Stay up to date with what we have been doing with our partners, how we're working with them to help our customers and what our partner experts are saying.

Filter:
- Adobe
- AMD
- Apple
- AppSense
- Aruba
- ASUS
- Belkin
- Brother
- Bullitt
- CAT Phones
- Checkpoint
- Cisco
- Cisco (Featured)
- Cisco Energy Management
- Cisco Energy Management (Featured)
- Cisco>Cisco
- Citrix
- Clearswift
- Clearswift (Featured)
- Cloud
- Commvault
- COVID-19
- Cyber
- Dell
- Digital Workplace
- EMC
- EMC (Featured)
- EPOS
- Epson
- F5
- F5 (Featured)
- Featured-1
- Fortinet
- Hitachi (Featured)
- Hitachi Data Systems
- HP
- HP (featured)
- HP>HP Converged Systems (Featured)
- HP>HP PC
- HP>HP PC (Featured)
- HP>HP Print
- HP>HP Print (Featured)
- HPE
- HPE>HP 3Par Storage
- HPE>HP 3Par Storage (Featured)
- HPE>HP Converged Systems
- Hybrid Infrastructure
- Hypertec
- IBM
- IBM (Featured)
- IBM>IBM Business Analytics
- IBM>IBM Business Analytics (Featured)
- IBM>IBM Emergency Response Services
- IBM>IBM Emergency Response Services (Featured)
- IBM>IBM Mobile Device Management
- IBM>IBM Mobile Device Management (Featured)
- IBM>IBM Power 8 Systems
- IBM>IBM Power 8 Systems (Featured)
- IBM>IBM Smarter Storage
- IBM>IBM Smarter Storage (Featured)
- iiyama
- Industry
- Infrastructure
- Intel
- Ivanti
- Lenovo
- Lenovo>Lenovo Data Centre Group (DCG)
- Lenovo>PC
- LG
- Logitech
- Microsoft
- Microsoft (Featured)
- Mimecast
- Mimecast (Featured)
- MobileIron
- MobileIron (Featured)
- NEC
- NEC (Featured)
- NetApp
- NetApp (Featured)
- Nutaix
- Nutanix
- Nuvias & Riverbed
- Oracle
- Oracle (Featured)
- Oracle>Oracle Converged Infrastructure
- Oracle>Oracle Converged Infrastructure (Featured)
- Oracle>Oracle Systems Consolidation
- Oracle>Oracle Systems Consolidation (Featured)
- Palo Alto
- Philips
- Philips (Featured)
- Plantronics
- Polycom
- Product
- Product (Featured)
- Qlik
- Quest
- Recent-Home
- Red Hat
- Remote working
- RES
- RSA
- Samsung
- SanDisk
- SCC News
- Security
- Software
- Symantec
- Symantec (Featured)
- Toshiba
- Uncategorised
- Uncategorized
- VCE
- VCE (Featured)
- Veeam
- Veritas
- VMware
- VMWare (Featured)
- ZAGG
- Zebra

Cisco is saying goodbye to Spark branding and incorporating the offering under its WebEx platform as partners are struggling to differentiate between the two offerings. Nirav Sheth, VP of architectures, solutions and engineering for Cisco’s Global Partner Organization, explained that this was a response to partner concerns over how to differentiate between the two products....
Cisco rebrands Spark as WebEx to simplify partners’ go to market

[pdf-embedder url=”https://www.scc.com/wp-content/uploads/2018/06/Datasheet_-_SteelCentral_Aternity.pdf” title=”SteelCentral Aternity Datasheet.”] For more information please click here.
SteelCentral Aternity Datasheet

Microsoft first revealed the Surface Hub in January 2015, although it didn’t start shipping the mammoth collaborative toolset until March 2016 after initial delay. Despite the fact that the last significant Surface Hub news came five months ago, Microsoft today is building momentum around version two in a surprise pre-announcement: Surface Hub created an entirely...
Microsoft is working on Surface Hub 2
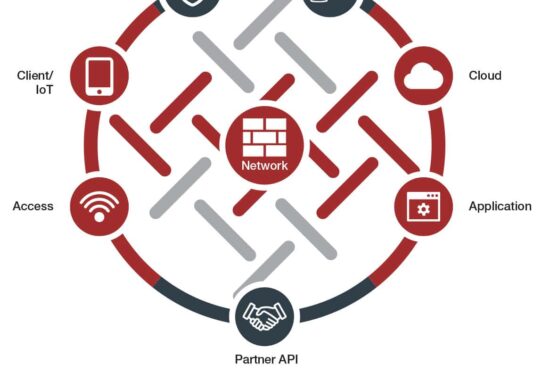
Nearly two years ago, Fortinet unveiled their technology vision of the Fortinet Security Fabric. With the release of FortiOS 6.0, they have turned that vision into a full-fledged reality with a truly integrated and automated security framework designed for today’s dynamic networks. FortiOS is already the world’s most deployed network security operating system, and this...
Innovation Insights: Our Security Fabric Vision is Reality
Dell Inc. announces it has been recognised by the Ethisphere Institute, a global leader in defining and advancing the standards of ethical business practices, as one of the 2017 World’s Most Ethical Companies. This is the fifth consecutive year Dell has been recognised. It is one of only three honourees in the technology industry, underscoring...
Dell Inc. Named One of World’s Most Ethical Companies® for 2017
Today, organisations are challenged with exponential data growth, and rely on multiple backup and data protection solutions to manage their data. Even then, they lack confidence that their data is backed up and protected. When used together with our Alliances backup appliances solutions, Veeam® provides the industry’s leading combination of secondary storage and Availability software,...
A Guide to Backup Appliances and Data Availability
After further investigation, Cisco has identified additional attack vectors and features that are affected by this vulnerability. In addition, it was also found that the original fix was incomplete so new fixed code versions are now available. Please see the Fixed Software section for more information. A vulnerability in the XML parser of Cisco Adaptive Security Appliance...
Cisco Adaptive Security Appliance Remote Code Execution and Denial of Service Vulnerability
Check Point is proud to announce that we have received two ‘Cyber Essentials Plus’ awards under the British Government’s Cyber Essentials Accreditation Scheme. The British Ambassador to Israel, David Quarrey, officially presented the accreditations as part of the UK Government’s Cyber Essentials Scheme. Launched in 2014, the Cyber Essentials Scheme serves as part of the...
Check Point Security Credentials Validated with Cyber Essentials Plus Awards
It’s here. Cisco has solved one of the biggest challenges facing the security industry – and now thousands of Cisco customers can start using this breakthrough new network security technology. Back in June, Cisco announced Encrypted Traffic Analytics – a breakthrough technology that identifies malware in encrypted traffic, without having to break apart the packets...
Cisco extends Encrypted Traffic Analytics to Nearly 50,000 Customers
Set yourself up for success in 2018 by participating in our January SophSkills program. Each 30-min session is designed to give you the know-how you need to maximize your Intercept X sales. Either attend the live presentations or watch the recordings at your leisure. From sales skills to technical demos and objection handling, there’s something...
Maximize your Intercept X Sales with January SophSkills Training
IBM have announced a new IBM Cloud Private Software platform to help companies unlock billions in technology investment in core data and applications and extend cloud-native tools across public and private clouds. IBM Cloud Private Software is designed to enable companies to create on-premises cloud capabilities similar to public clouds to accelerate app development. The...
IBM Brings Cloud-native Environment to Private Clouds
Arnold H. Glasow famously quipped that “the trouble with the future is that it usually arrives before we’re ready for it.” The past year certainly took us by surprise when the WannaCry and Petya ransomware outbreaks hit businesses globally, causing unprecedented disruption, while serious new vulnerabilities such as BlueBorne were discovered in almost every connected...